“Vulnerability Details” View Explained
Everything you need to know about a particular vulnerability in one place—from related assets, severity, and summary to date last seen and creating support tickets.
Whenever you click on the name of an issue in the “Issues” tab or from the “Asset details” view, you see a window that details everything about that issue.
What is There in the “Vulnerability Details” View
The “Vulnerability details” view aims to provide you with actionable information about the issue to simplify and streamline remediation efforts.
At the very top, next to the name, it offers the most important information in rounded rectangles:
- Severity level and CVSS score
- Status: open, fixed, accepted risk, or false positive
- EPSS Score
- EPSS Percentile (measure of probability relative to other scores)
- CWE number with a link to Mitre’s CWE database
- CVE number with a link to NIST’s NVD database
- CISA KEV Status: "detected" if the issues is in the CISA database of known exploited vulnerabilities and "not detected" if it isn't.

Next to it are the buttons that correspond to the actions you can perform with the issue:
- Set status (again, it’s open, fixed, accepted risk, or false positive)
- Create a Jira ticket with information about the vulnerability (which will work if you have the integration with Jira set up)
- Copy link to send it to other people on your team

If you click “Create Jira ticket” and you have the integration in place, an additional prompt will appear to confirm you indeed want to add the issue to the tracker.

Below, Attaxion lists other valuable data regarding this particular instance of the issue.
- When was it last seen
- When was it first seen
- Its lifetime (how much time has passed between dates first and last seen)
- Affected asset (domain, IP address, or other asset type)
- Related root asset.
- CISA KEV details if the CISA KEV status is "detected"

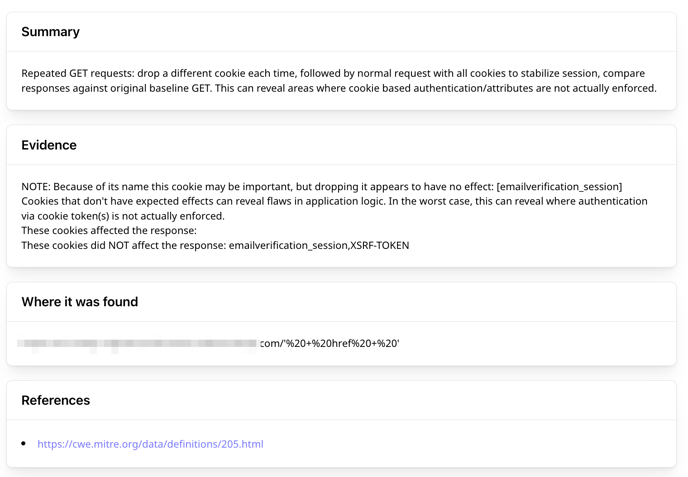
Attaxion also provides information that the security team will require to fix the issue:
- Summary: A quick explanation of what this issue is about.
- Evidence (optional): Whatever points to the issue’s existence.
- Where it was found (optional): The exact address.
- Solution: A recommended way of fixing it.
- References: A list of articles about this issue from different sources, which, on the one hand, were used to inform the summary and the solution, and on the other hand, can provide some additional information that could be useful for remediation.
Finally, below you can find the list of assets that are affected by the same vulnerability.
You can also refresh the list of assets (it will not trigger a scan though), and export it as a CSV file.
