How to Generate and Export a Vulnerability Report
Customize, generate, and export vulnerability reports for your entire external attack surface or specific assets.
Attaxion allows users to generate vulnerability reports.
To start, go to the reports tab by clicking “Reports” in the menu on the left. To create a new report, click the “Create report” button in the upper-right corner of the screen.
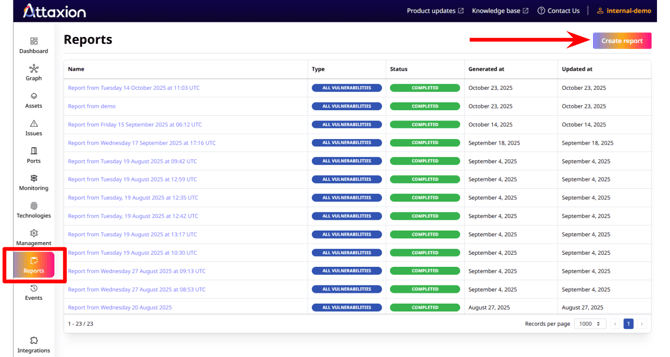
Fill out the “New report” form with the report type (currently, only the ‘All Vulnerabilities’ report type is available and selected by default, but that will change soon with the upcoming releases) and the report name (if you don’t like the default one).
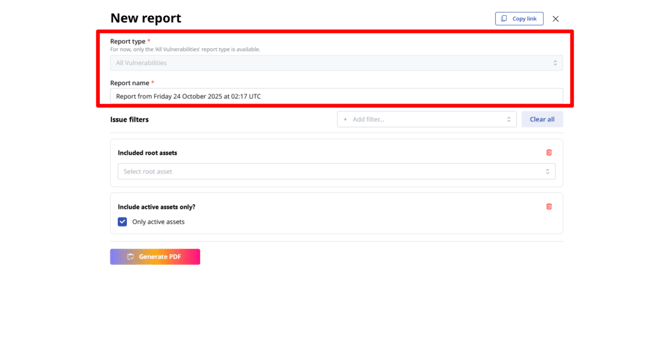
You can select one or more specific root assets or several — the report will include them and all their child assets. You can also choose to include only active assets or both active and inactive. By default, the “Only active assets” checkbox is selected.
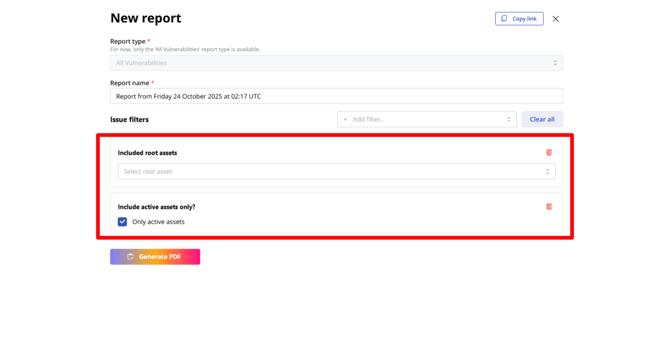
You can customize your report by adding additional filters. To do that, click on the “Add filter” dropdown menu. The available filters are:
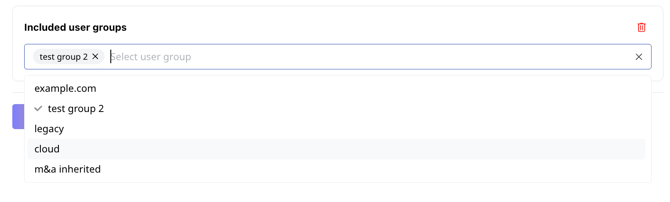
- Included user groups
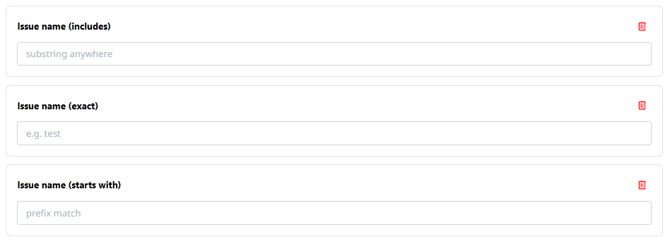
- Issue name (includes, exact, or starts with)
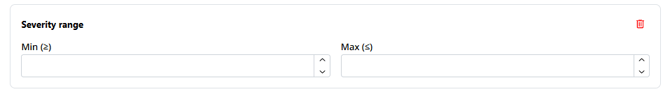
- Severity range (from 0 to 10)
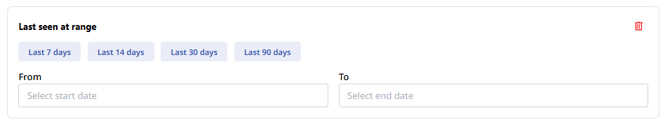
- Last seen range
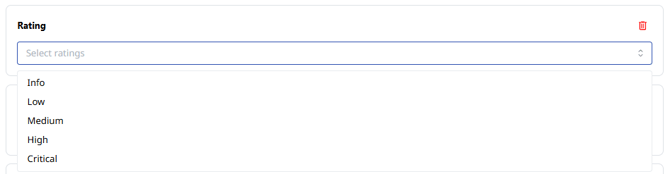
- Severity rating
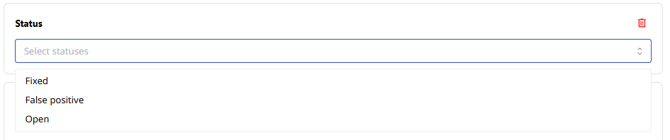
- Status (open, fixed, or false positive)
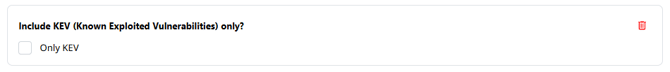
- Include KEV (Known Exploited Vulnerabilities) only?
You can combine multiple filters or remove them by clicking the trash icon on the right side of each added filter.
After setting the filters and other report elements, you can now click “Generate PDF.” This action will save the report so you can use it in the future, generate it, and automatically start the download of the report in PDF format.
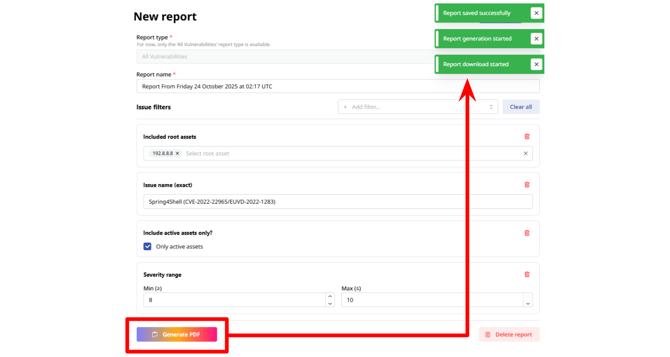
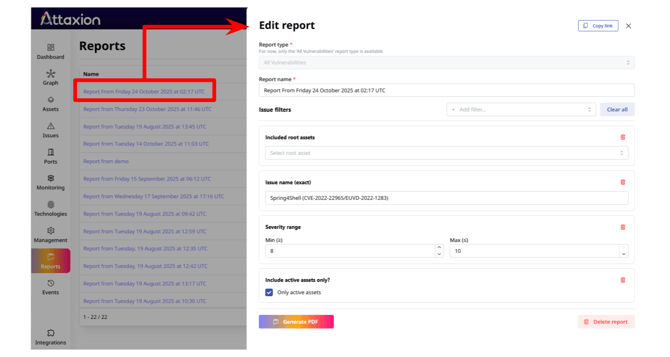
The report will be listed in the Reports window, and you will be able to edit it by changing the settings and regenerating it again, generate a new and updated version of the report, or delete it.
What Does the Report Contain?
The exported report contains the Cover, Overview, and Vulnerability details pages. The Cover page shows the the date the report was generated and the number of targets scanned.
Meanwhile, the Overview page shows the distribution of security issues by severity level. It also contains two tables listing the most recently detected issues and the top 10 most severe issues.
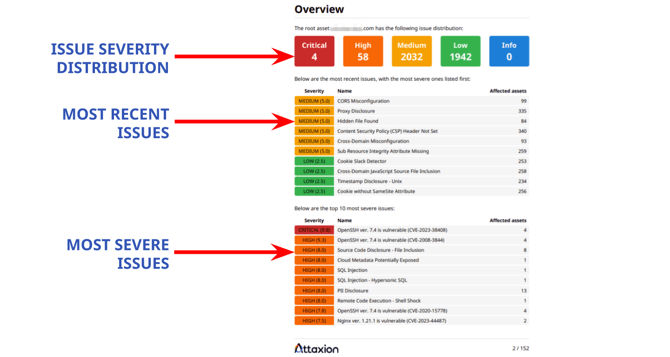
The succeeding pages are dedicated to each individual detected vulnerability, showing data that can also be found in the Vulnerability Details view, such as the severity levels and CVSS scores, first and last seen dates, number of affected assets, and CWE and CVE codes, where applicable.
A detailed description of each issue and the recommended mitigation steps are also available, along with a complete list of all affected assets.
